China’s Cybersecurity Regulator Issues Draft Measures on Incident Reporting
The Cybersecurity Administration of China (CAC), China’s cybersecurity regulator, has issued a new set of draft measures outlining requirements for companies to report network security incidents. The Administrative Measures for Cybersecurity Incident Reporting (Draft) (“draft measures”), based on China’s 2017 Cybersecurity Law, seeks to decrease the harm and damage caused by security incidents and maintain national cybersecurity.
If passed in their current form, any network operator that builds or operates networks or provides online services (hereinafter collectively referred to as “operators”) are required to report any incident that threatens network security with the potential to cause significant harm to relevant government bodies.
The types of incidents that need to be reported under the draft measures are mostly those that involve harm or threats to government institutions and infrastructure, such as government and party websites and utility infrastructure, as well as any incidents that can cause wider economic damage or harm to the general population.
The CAC will be soliciting feedback from the public on the draft measures until January 7, 2024.
Security incident reporting obligations
The draft measures broadly define “network security incidents” as “incidents caused due to human error, software and hardware defects or failures, natural disasters, or other scenarios that cause harm to networks and information systems or the data stored therein, resulting in a negative impact on society”.
When a network security incident occurs, operators are required to initiate an emergency plan at the earliest possible time. However, an operator is only required to report an incident if it falls under one of three high-risk categories: a “significant” incident, “serious” incident”, or “very serious” incident. It is these three types of incidents that the draft measures concern themselves with.
Threat-level classification of security incidents
The draft measures have been released along with a Cybersecurity Incident Classification Guide, which can be downloaded from the link with the draft measures (attachment 1; 附件1). This Guide provides the definitions and parameters for the classification of a security incident.
Broadly, the situations in which an incident is considered significant, serious, or very serious are:
- Where an important network and information system suffers system losses, causing widespread system paralysis and loss of business processing capabilities.
- Where national secrets, important sensitive information, and important data are lost or stolen, tampered with, or counterfeited, posing a threat to national security and social stability.
- Other network security incidents that pose threats and have particularly serious impacts on national security, social order, the economy, and public interests.
The Guide also provides more granular parameters for determining which category an incident falls into, which we have summarized in the table below.
| Network Security Incident Threat Classification | |||
| Significant incident (较大) | Serious incident (重大) | Very serious incident (特别重大) | |
| 1 | Party and government agency portal websites at or above the prefecture city-level* and key news websites are inaccessible for more than two hours due to an attack or malfunction. | Party and government agency portal websites at or above the prefecture city-level and key news websites are inaccessible for more than six hours due to an attack or malfunction. | Party and government agency portal websites at or above the prefecture city-level and key news websites are inaccessible for more than 24 hours due to an attack or malfunction. |
| 2 | The entire critical information infrastructure is interrupted for more than 30 minutes or its main functions are interrupted for more than two hours. | The entire critical information infrastructure is interrupted for more than two hours or its main functions are interrupted for more than six hours. | The entire critical information infrastructure is interrupted for more than six hours or its main functions are interrupted for more than 24 hours. |
| 3 | The work and livelihoods of more than 10 percent of the population in a single prefecture-level administrative district are affected. | The work and livelihoods of more than 30 percent of the population in a single prefecture-level administrative district are affected. | The work and livelihoods of more than 30 percent of the population in a single provincial-level* administrative district are affected. |
| 4 | Water, electricity, gas, oil, heating or transportation provision for more than 100,000 people is affected. | Water, electricity, gas, oil, heating or transportation provision for more than 1 million people is affected. | Water, electricity, gas, oil, heating or transportation provision for more than 10 million people is affected. |
| 5 | Important data is leaked or stolen, posing a relatively serious threat to national security and social stability. | Important data is leaked or stolen, posing a serious threat to national security and social stability. | Important data is leaked or stolen, posing a very serious threat to national security and social stability. |
| 6 | The personal information of more than 1 million people has been leaked. | The personal information of more than 10 million people has been leaked. | The personal information of more than 100 million people has been leaked. |
| 7 | Party and government agency portal websites, key news websites, and online platforms are attacked and tampered with, resulting in the widespread dissemination of illegal and harmful information.
In the following situations, the information can be considered have been disseminated on a “relatively large scale” (较大范围):
|
Party and government agency portal websites, key news websites, and online platforms are attacked and tampered with, resulting in the widespread dissemination of illegal and harmful information.
In the following situations, the information can be considered have been disseminated on a “large scale” (大范围):
|
Party and government agency portal websites, key news websites, and online platforms are attacked and tampered with, resulting in the widespread dissemination of illegal and harmful information.
In the following situations, the information can be considered have been disseminated on a “very large scale” (特大范围):
|
| 8 | Causes direct economic losses of more than RMB 5 million (US$697,798). | Causes direct economic losses of more than RMB 20 million (US$2.8 million). | Causes direct economic losses of more than RMB 100 million (US$14 million). |
| 9 | Other network security incidents that pose a relatively serious threat and have a relatively large impact on national security, social order, the economy, and public interests. | Other network security incidents that pose a serious threat and have a large impact on national security, social order, the economy, and public interests. | Other network security incidents that pose a very serious threat and have a very large impact on national security, social order, the economy, and public interests. |
| *Referring to the government institutions of a prefecture-level city, the second level within China’s administrative division system; e.g. Guangzhou, Chengdu.
**Referring to the government institutions of a province or municipality (直辖市), the first level within China’s administrative division system; e.g. Guangdong, Shanghai. |
|||
A fourth category, called “general” network security incidents”, is simply defined as “network security incidents that pose a certain threat and have a certain impact on national security, social order, the economy, and public interests” in the Guide.
Incident reporting requirements based on threat level
Security incidents that are classified as “major”, “serious”, or “very serious” as outlined in the table should be reported within one hour.
Meanwhile, if the implicated network or system belongs to a department of a central or state agency, or one of the companies and institutions that are under their management, the operator must first report the incident to the cybersecurity and information work organization within that department.
If it is a “serious” or “very serious” incident, it is then the responsibility of this organization to report it to the national network and information department (国家网信部门) within one hour of receiving the report from the relevant department.
If the implicated network or system is critical information infrastructure, the operators must report the incident to the protection work departments (保护工作部门) and public security organs.
Under China’s critical information infrastructure security protection regulations, the protection work departments are government organs tasked with guiding and supervising the protection of critical information infrastructure operators (CIIO).
In the event of a serious or very serious incident, the protection work department shall report it to the national cyberspace department and the public security department of the State Council within one hour of receiving the report.
Other network and system operators should report to the local cybersecurity and information department. If it is a serious or very serious incident, the local cybersecurity and information department must report it to the higher-level cybersecurity and information department within one hour of receiving the report.
If the operator has an industry supervisory department, then it must also report the incident in accordance with this department’s requirements. In addition, if there is suspicion that a crime has been committed, the operator must also report the incident to the public security organs at the same time.
Reporting a security incident
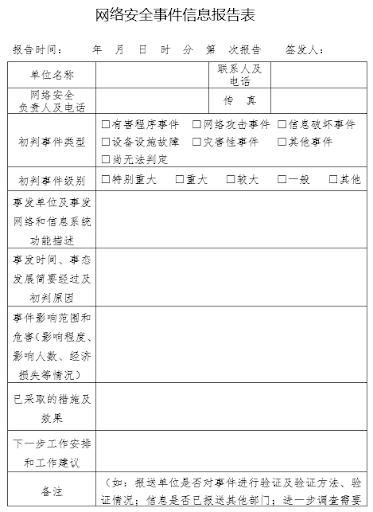
Operators can report incidents in accordance with the Cybersecurity Incident Information Reporting Form, which can be downloaded from the link with the draft measures (attachment 2; 附件2).
The following information must be included in the form:
- The name of the entity where the incident occurred and basic information about the facilities, systems, and platforms in which the incident occurred;
- The time and place when the incident was discovered or occurred, the type of incident, the impact and harm caused, and any measures taken and their effects. For ransomware attacks, the ransom amount, method, date, and other information on the ransom’s payment should also be included;
- Information on how the situation is developing and possible further impacts and harms;
- Preliminary analysis of the cause of the incident;
- Clues that can assist with further investigation and analysis, including information on the possible attacker, attack routes, existing vulnerabilities, and so on;
- Further response measures that will be taken and requests for support;
- The protection conditions at the incident site; and
- Any other information or situations that should be reported.
If the cause, impact, or developments of the incident cannot be determined within the one hour reporting window, then the entity can first report items one and two in the list above. The other information and circumstances must then be reported within 24 hours.
In addition, if any new information or development arises during the investigation process after the incident is reported, the entity should report it in a timely manner.
Post-reporting obligations and liabilities
After the incident has been handled, the operator must conduct a comprehensive analysis and summary of the cause of the incident, covering various matters such as the emergency response measures adopted, threats posed, responsibilities, the situation regarding rectification, lessons learned and so on. This report must be submitted to the same authority to which the incident was originally reported within five working days.
Organizations or individuals providing services to an operator who discover a major, serious, or particularly serious security incident in the operator’s networks or systems must let the operator know and remind them to report the incident to the relevant authority. If the operator intentionally conceals the incident or refuses to report, then the organization or individual can report this to the local cyberspace department or the national cyberspace department.
Social organizations and individuals are also encouraged to report major, serious, or very serious security incidents that occur to the cybersecurity and information departments.
Operators that fail to report a security incident as required may be penalized by the network information department “in accordance with relevant laws and administrative regulations”; however, the draft measures do not specify which regulations these are.
Operators and any responsible persons may also be liable to more severe penalties if they delay the report, omit details, lie, or conceal matters related to the security incidents in the report, resulting in significantly harmful consequences.
If an operator thoroughly complies with the reporting requirements, has taken reasonable measures to protect its networks, and done its utmost to reduce the impact of the incident, it may be exempted from punishment or be given a lighter penalty, depending on the circumstances.
Limitations of the draft regulations
The draft regulations have similar limitations to other cybersecurity and data protection regulations in China, most notably a lack of clear definitions for key terms and unclear parameters.
For instance, the authorities have still not provided an official definition or released a reference guide for what constitutes “important data”. This issue has long been a headache for companies in other areas of cybersecurity and data protection, such as the requirements for cross-border data transfer (which impose limitations on the export of “important data”).
In fact, providing a clearer definition for “important data” was among the suggestions provided in the European Chamber of Commerce’s European Business in China Position Paper 2023/2024 released in September 2023, urging for “the scope of important data to be clearly and narrowly defined, with regulators providing a sufficient grace period between any future releases of guidelines related to the definition of ‘important data’ and catalogues, and their implementation”.
Other uncertainties also remain, such as exactly which companies are considered CIIOs and what is “important sensitive information” (China’s Personal Information Protection Law (PIPL) defines “sensitive personal information”, although it does not appear to be the same as the information that the draft measures are referring to).
In addition, some of the parameters of the various incident threat levels default to somewhat vague language, such as livelihoods “affected” and “incidents that pose a serious threat”, which leave room for interpretation.
All of these issues could make it difficult for entities to accurately assess whether an incident needs to be reported and may lead to either over- or under-reporting. It could also leave companies vulnerable to penalties due to being unaware that they were required to report an incident.
However, the draft measures are still open for public comment, and it is possible that some of these issues will be addressed before the final version is released and adopted. Additional regulations clarifying some of these terms may also be released in the meantime. Companies are advised to keep an eye on developments on this and related regulations. They may also begin to assess whether any of their current data, information, or operations could fall under the scope of the draft measures in the event of a security incident and prepare relevant contingency plans that factor in the potential requirements for incident reporting.
About Us
China Briefing is written and produced by Dezan Shira & Associates. The practice assists foreign investors into China and has done so since 1992 through offices in Beijing, Tianjin, Dalian, Qingdao, Shanghai, Hangzhou, Ningbo, Suzhou, Guangzhou, Dongguan, Zhongshan, Shenzhen, and Hong Kong. Please contact the firm for assistance in China at china@dezshira.com.
Dezan Shira & Associates has offices in Vietnam, Indonesia, Singapore, United States, Germany, Italy, India, Dubai (UAE), and Russia, in addition to our trade research facilities along the Belt & Road Initiative. We also have partner firms assisting foreign investors in The Philippines, Malaysia, Thailand, Bangladesh.
- Previous Article 2023 Chinese Visa Application Guidelines
- Next Article Digital Recruitment in China: Definition, Strategies, and Best Practices